The WordPress REST API holds significant importance in modern web development as it bridges the gap between content management systems (CMS) like WordPress and the evolving landscape of web applications, services, and digital experiences.
The role of WP REST API in enabling custom integrations, mobile app development, decoupled architectures, and other modern web practices cements its importance in contemporary web development strategies.
In other words, the REST API exposes your WordPress website’s content, such as posts, pages, users, and more, in a format that’s easily consumable by other software applications. It could include
Mobile Apps
- A news app fetching and displaying the latest blog posts from your WordPress website
- An e-commerce app showing product listings and details from your WooCommerce-powered content management system.
- An event app displaying upcoming events from your WordPress-based event management site
Web Applications
- A marketing dashboard aggregating content statistics from multiple WordPress websites
- A custom portfolio website pulling project data from a WordPress backend
- A job board platform integrating job listings from different WordPress sites
Single-Page Applications (SPAs)
Third-Party Platforms
- A content aggregation platform displaying articles from various WordPress blogs
- A learning management system (LMS) incorporating educational content from WordPress websites
- A social media dashboard pulling posts and updates from multiple WordPress-based social profiles
- Membership websites managing user enrollment, progress tracking, and content access seamlessly
IoT (Internet of Things)
- A weather station device sending data to a WordPress website via its REST API for real-time weather updates
- A smart home application accessing sensor data from a WordPress backend to control home automation
Cross-Platform Applications
- A hybrid mobile app (built with tools like Ionic or React Native) displaying content from a WordPress site alongside native app features
- A progressive web app (PWA) using WordPress data to provide offline-accessible content and app-like experiences
Chatbots and Voice Assistants
- A chatbot pulling FAQ content from a WordPress knowledge base
- A voice-activated assistant retrieving information from a WordPress site’s REST API in response to user queries
Data Analytics and Reporting
- A business intelligence dashboard integrating sales and marketing data from a WordPress-based e-commerce site
- An analytics tool visualizing user engagement metrics gathered from WordPress content
These examples demonstrate the versatility of the WordPress REST API in connecting WordPress data with a diverse range of applications, services, and platforms to create innovative and interconnected digital experiences.
At the same time, it exposes how vulnerable your WordPress website can be with REST API constantly exchanging data every other second.
Fortunately, we are here to discuss 5+ best practices for securing your WordPress REST API.
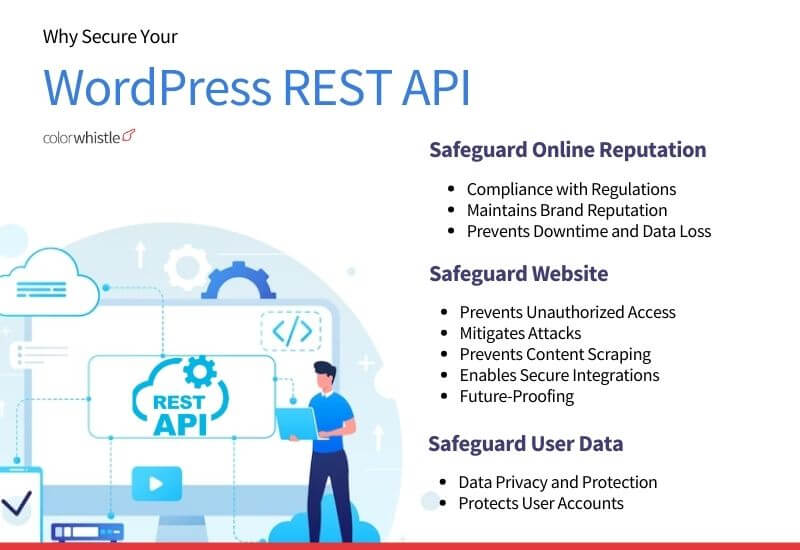
Why Securing your WordPress REST API is Crucial?
Safeguards Website
- Prevents Unauthorized Access
- Mitigates Attacks
- Prevents Content Scraping
- Enables Secure Integrations
- Future-Proofing
Safeguards User Data
- Data Privacy and Protection
- Protects User Accounts
Safeguards Online Reputation
- Compliance with Regulations
- Maintains Brand Reputation
- Prevents Downtime and Data Los
5 Best Practices for Securing WP REST API
- Choose strong authentication methods
- Implement user role and permissions
- Rate limiting and IP whitelisting
- Input validation
- Security plugins and tools
TIP#1: Choose Strong Authentication Methods
- Implement robust authentication methods such as token-based authentication, OAuth 2.0, or API Key. This ensures that only authorized users or applications can access your API.
Token-based authentication
Benefits
Drawbacks
Security: Tokens are typically random and unique, providing a high level of security. They can also be short-lived, reducing the window of vulnerability if compromised.
User Experience: Tokens can be stored in cookies or local storage, allowing users to stay authenticated even if they close the browser.
Granular Control: Tokens can be associated with specific permissions, allowing fine-grained access control.
Scalability: Tokens are self-contained, reducing the need for server-side storage, which aids in scaling.
Storage: Tokens can be stored on the client side, making them susceptible to theft through XSS attacks.
Complexity: Implementing token-based authentication requires handling token creation, validation, and expiration.
Stateless: The server doesn’t store token information, which can make handling revoked tokens challenging.
When to Use:
Use token-based authentication when you need to provide secure, granular access control, and have the ability to handle token management. It’s suitable for applications where user experience and scalability are priorities.
Did You Know?
Token-based authentication is suitable for secure, user-friendly experiences.
You can implement token-based authentication using plugins like JWT Authentication for WP-API or the Application Passwords plugin that is merged into WP core version 5.6.
OAuth 2.0
Benefits
Drawbacks
Third-Party Access: OAuth 2.0 enables third-party applications to access users’ data without exposing user credentials.
User Consent: Users have control over which permissions they grant to third-party apps.
Token Revocation: OAuth 2.0 supports token revocation, enhancing security.
Single Sign-On (SSO): OAuth 2.0 can be used to implement single sign-on across multiple services.
Complexity: Implementing OAuth 2.0 can be complex due to its various flows (Authorization Code, Implicit, Client Credentials, etc.).
Token Lifetime: Tokens can have long lifetimes, increasing the risk if they are compromised.
Standard Variability: Different implementations of OAuth 2.0 might have varying security measures.
When to Use:
Use OAuth 2.0 when you want to enable third-party applications to access user data securely without sharing credentials. It’s ideal for scenarios where user consent, SSO, and secure API access by external services are important.
Did You Know?
OAuth 2.0 is ideal for third-party access and SSO.
API Key Authentication
Benefits
Drawbacks
Simplicity: API keys are straightforward to implement and require minimal infrastructure.
Immediate Access: API keys allow immediate access without the need for complex token generation.
Controlled Access: API keys can be tied to specific applications or services, providing basic access control.
Security: If API keys are exposed or transmitted insecurely, they can be easily exploited.
Revocation: Revoking API keys might require manual intervention and reissuing keys to legitimate users.
Limited Control: API keys lack the granularity of permissions and access the control offered by tokens.
When to Use:
Use API key authentication when you need a simple method for controlling access to your API. It’s suitable for public APIs where security requirements are relatively lower, or for internal APIs where security concerns are manageable.
Did You Know?
API key authentication offers simplicity and basic access control.
TIP#2: Implement User Roles and Permissions
- Follow the principle of least privilege by assigning specific capabilities to user roles.
- Restrict roles to only the permissions they need to access the API.
- Use WordPress’s built-in user roles (administrator, editor, contributor, etc.) to control API access based on user privileges
Here’s how WordPress user roles can be used to control API access:
- Administrator Role: Administrators can perform all CRUD (Create, Read, Update, Delete) operations on the API endpoints.
- Editor Role: Editors can access most API endpoints related to posts, pages, and media, allowing them to create, edit, and delete content.
- Author Role: Authors have access to the API endpoints for creating and updating posts, but their permissions are limited to their own posts.
- Contributor Role: Contributors have access to limited API endpoints and can only manage their own drafts.
- Subscriber Role: Subscribers have very limited access to the API, typically only being able to retrieve their user profile information.
In WordPress, capabilities are the specific permissions that define what actions users of different roles can perform.
By assigning or modifying capabilities, you can control the level of access a user role has to different parts of your website, including the REST API.
Here are examples of how to assign specific capabilities to roles to limit API actions:
EXAMPLE I: Limiting Editor Access to API
In this example, we’ll limit the “Editor” role to only have read (GET) access to the REST API endpoints related to posts.
function restrict_editor_api_access() {
// Get the "Editor" role object
$editor_role = get_role('editor');
// Remove the capability to create, update, or delete posts via API
$editor_role->remove_cap('edit_posts');
$editor_role->remove_cap('edit_others_posts');
$editor_role->remove_cap('edit_published_posts');
$editor_role->remove_cap('delete_posts');
$editor_role->remove_cap('delete_published_posts');
}
add_action('init', 'restrict_editor_api_access');
EXAMPLE II: Allowing Author Access to API for Their Own Posts
In this example, we’ll allow the “Author” role to have read and write (GET, POST, PUT, DELETE) access to their own posts via the REST API.
function allow_author_api_access() {
// Get the "Author" role object
$author_role = get_role('author');
// Add the capability to read and write their own posts via API
$author_role->add_cap('read');
$author_role->add_cap('edit_posts');
$author_role->add_cap('delete_posts');
}
add_action('init', 'allow_author_api_access');
EXAMPLE III: Custom Role with Restricted API Access
In this example, we’ll create a custom role named “Content Manager” with limited API access, allowing them to read and create posts, but not update or delete them.
function create_custom_role() {
add_role('content_manager', 'Content Manager', array(
'read' => true,
'edit_posts' => false,
'delete_posts' => false,
'publish_posts' => false,
'upload_files' => true, // Allow uploading media
));
}
add_action('init', 'create_custom_role');
TIP#3: Rate Limiting and IP Whitelisting
Rate limiting and IP whitelisting are both important security measures, but they serve different purposes and address distinct aspects of protecting systems and APIs. Here’s a comparison of the two:
Parameter
Rate Limiting
IP Whitelisting
Purpose
Rate limiting restricts the number of requests a user, IP address, or client can make to a system or API within a specific time frame.
IP whitelisting restricts access to a system, service, or API based on a predefined list of approved IP addresses.
Objective
The primary goal of rate limiting is to prevent abuse, unauthorized access, and overload of the system’s resources.
The main goal of IP whitelisting is to enhance security by allowing only trusted IPs to interact with the system.
Mechanism
It involves tracking the number of requests made by a user or IP address within a defined time frame and enforcing a maximum limit on requests. Exceeding the limit leads to either delayed processing or rejection of additional requests.
It involves configuring the system to only accept incoming requests from IP addresses listed on the whitelist. Requests from non-whitelisted IPs are automatically denied.
Granularity
Rate limiting can be granular, allowing different users or groups to have different rate limits based on their roles or privileges.
IP whitelisting is generally less granular compared to rate limiting, as it focuses on controlling access at the IP level.
When to Use Each:
- Use Rate Limiting when you want to prevent abusive usage, maintain performance during high traffic, and ensure fair access to resources.
- Use IP Whitelisting when you want to enhance security by allowing only specific, trusted IPs to access sensitive systems or services and limit exposure to potential threats.
- In some scenarios, you might combine IP whitelisting with rate limiting to provide additional layers of security for critical systems or APIs.
TIP#4: Input Validation
- Input validation is a fundamental security practice that should be integrated into the development process to safeguard web applications against SQL injection, XSS, and other vulnerabilities arising from user-generated content.
Here’s how you can go about it:
- SQL Injection Prevention: SQL injection occurs when malicious SQL code is injected into input fields.
When working with databases, always use parameterized queries or prepared statements to prevent SQL injection. Here’s an example using PDO (PHP Data Objects)
$userId = $_GET['user_id'];
$stmt = $pdo->prepare("SELECT * FROM users WHERE id = :id");
$stmt->bindParam(':id', $userId, PDO::PARAM_INT);
$stmt->execute();
- XSS Prevention: Cross-site scripting involves injecting malicious scripts into a website, which are then executed in users’ browsers.
To prevent cross-site scripting, escape user-generated content before rendering it in HTML.
$username = $_GET['username']; echo htmlspecialchars($username, ENT_QUOTES, 'UTF-8');
Always remember that input validation is just one layer of security. It’s important to combine it with other security practices, such as output encoding, rate limiting, and authentication, to ensure a robust security posture for your API.
TIP#5: Integrate Security Plugins and Tools
These plugins add firewall protection, intrusion detection, and malware scanning to your website security strategy. It’s important to regularly update and configure these security tools to ensure their effectiveness against evolving threats.
Other Common Practices for Securing Your WP REST API
- Secure Data Transmission: Use HTTPS to encrypt data transmission between clients and your server. Set up and configure SSL/TLS certificates for your WordPress site. This ensures that data remains confidential and prevents eavesdropping or data manipulation.
- Keep WordPress Core, Themes, and Plugins Updated: Regularly update your WordPress installation, themes, and plugins to ensure you’re protected against known security vulnerabilities. Remove unused plugins and themes, as they can be potential points of entry for attackers.
- Logging and Monitoring: Monitor your API usage and log API activities to detect suspicious or unauthorized behavior. Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
Key Takeaways
The REST API is not limited to integrating only with WordPress websites.
Representational State Transfer (REST) is an architectural style and set of principles for designing networked applications, particularly web services.
The REST API’s standardized use of HTTP methods (GET, POST, PUT, DELETE) and its reliance on JSON (JavaScript Object Notation) for data exchange are common practices in web development.
This means that you can integrate the REST API with various types of applications, services, and platforms, regardless of whether they are built using WordPress or not.
Incorporate the discussed best practices and secure your WordPress website when using REST API for custom web applications and business solutions.
Speaking of custom web applications, ColorWhistle has rich experience in working with WordPress developers and contributors worldwide. We have leveraged our technical expertise to support global businesses with innovative and reliable web-based applications.
Click here to write to us or call us at +1 (210) 787 3600 any time to discuss your business requirements. Our expert advisers respond to your messages swiftly.
What’s Next?
Now that you’ve had the chance to explore our blog, it’s time to take the next step and see what opportunities await!