CMS has a long history that goes back to the rise of the internet. Back in the day, websites were just static HTML pages that needed to be coded manually. It was a lot of work to update them. But with the advent of database-based websites, it became clear that people needed easier and more efficient ways to manage their content. That’s when the first CMS platforms came out in the late 1990s or early 2000s. It was a big change in the way we create, manage, and publish digital content. As a WordPress development company, in this blog, we’re going to take a closer look at the amazing journey of CMS and how it’s shaped modern web development.
Also Read
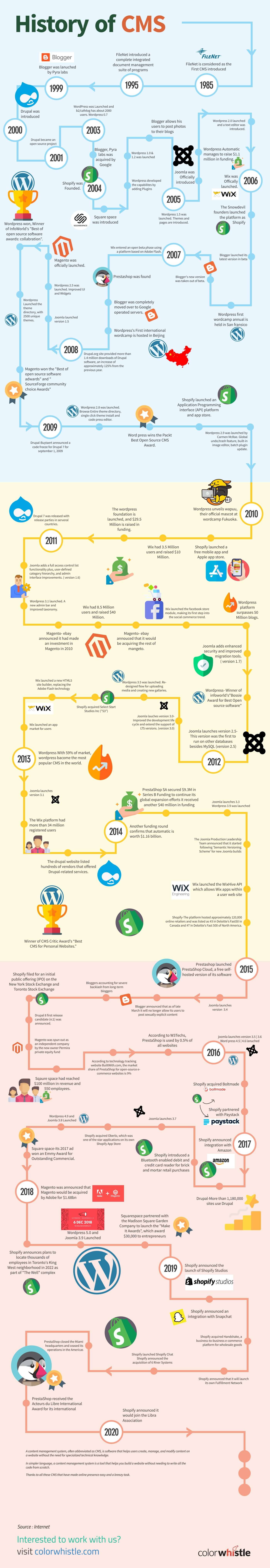
1985
FileNet is considered as the First CMS introduced
1995
FileNet introduced a complete integrated document management suite of programs
August 23, 1999
Blogger was launched by Pyra labs
May 18, 2000
Drupal was introduced
2001
Drupal became an open source project
May 27, 2003
WordPress was Launched and b2/cafelog has about 2000 users. WordPress 0.7
February 2003
Blogger, Pyra labs was acquired by Google
2004
Shopify was Founded.
2004
Square space was introduced
2004
WordPress developed the capabilites by adding Plugins
January 3, 2004
WordPress 1.0 was lanuched by Miles Davis.Minimalistic interface with performance improvements.
May 22, 2004
WordPress 1.2 was lanuched by Charlus Mingus. Came with ability to manage and develop plugins.
October 2004
Blogger’s Pyra Labs’ co-founder, Evan Williams, left Google
2004
Blogger allows his users to post photos to their blogs
February 17, 2005
WordPress 1.5 was launched by Billy strayhorn. Themes and pages are introduced.
August 17, 2005
Joomla was Officially introduced
September 2005
Joomla released Mambo 4.5.2.3 that combined other bug and moderate-level security fixes.( version 1.0)
October 2005
WordPress Automatic manages to raise $1.1 million in funding.
December 21, 2005
WordPress 2.0 launched and a text editor was introduced.
2006
Wix was Offically launched.
June 2006
The Snowdevil founders launched the platform as Shopify
August 14, 2006
Blogger launched its latest version in beta
August 2006
WordPress first wordcamp annual is held in San fransico
December 2006
Blogger’s new version was taken out of beta.
2007
Wix entered an open beta phase using a platform based on Adobe Flash.
January 22, 2007
WordPress 2.1 was launched by Ella Fitgerald. A new interface and an orthographic corrector.
May 2007
Blogger was completely moved over to Google operated servers.
May 16, 2007
WordPress 2.2 was launched by Stan Getz. Optimization of the loading speed of the CMS
Also Read
September 24,2007
WordPress 2.3 was launched by Dexter Gordon. Tags and user notification for CMS updates.
July 2007- June 2008
Drupal.org site provided more than 1.4 million downloads of Drupal software, an increase of approximately 125% from the previous year.
January 22, 2008
Joomla launched version 1.5
March 29, 2008
WordPress 2.5 was launched by Micheal Brecker. Improved UI and Widgets
July 15, 2008
WordPress 2.6 was launched by McCoy Tyner. Post revisons, word counts, image captions, theme previews and reordering of galleries.
December 10, 2010
WordPress 2.7 was launched by John Coltrane. Streamlined performance.
2008
WordPress won, Winner of InfoWorld’s “Best of open source software awards: collabration”.
2008
Magento won the “Best of open source software adwards” and ” SourceForge community choice Awards”
March 5, 2009
Drupal-Buytaert announced a code freeze for Drupal 7 for september 1, 2009
June 11, 2009
WordPress 2.8 was launched by Chet Baker. Browse Entire theme directory, single click theme install and code press editor.
December 18, 2009
WordPress 2.9 was launched by Carmen McRae. Global undo/trash feature, built-in image editor, batch plugin update.
From 2009-2012
Sqaure space grew an average of 266% in yearly revenue.
February 2010
WordPress unveils wapuu, their official mascot at wordcamp Fukuoka.
April 2010
Shopify launched a free mobile app and Apple app store.
2010
WordPress is the Winner of digitalsynergy’s “Hall of fame CMS category in the 2010 open source”
May 2010-April 2012
Prestashop grew from 17 employees to more than a hundred.
January 5, 2011
Drupal 7 was released with release parties in serveral countries.
January 10, 2011
Joomla adds a full access control list functionality plus, user-defined category hierarchy, and admin interface improvements. ( version 1.6)
February 23, 2011
WordPress 3.1 launched by Django Reinhardt. A new admin bar and improved taxonomy.
March 2011
Wix had 8.5 Million users and raised $40 Million.
June 2011
Wix launched the facebook store module, making its first step into the social commerce trend.
July 4, 2011
WordPress 3.2 was launched by George Gershwin. Fastera nd lighter with improvement typography, design and code.
July 19, 2011
Joomla adds enhanced security and improved migration tools. ( version 1.7)
December 12, 2011
WordPress 3.3 was launched by Sonny stitt. New drag-and-drop uploader, hover menus and pointer tips.
January 24, 2012
Joomla launches version 2.5-This version was the first to run on other databases besides MySQL (version 2.5)
November 6, 2013
Joomla launches version 3.2- Highlighting Content Versioning (version 3.2)
2013
The drupal website listed hundreds of vendors that offered Drupal-related services.
2014
Another funding round confirms that automatic is worth $1.16 billion.
Also Read
April 1, 2014
it received another $40 million in funding
April 30, 2014
Joomla launches 3.3- Improved password hashing and microdata and documentation powered by MediaWiki Translate extension. (version 3.3
May 15, 2014
Wix launched the WixHive API which allows Wix apps within a user web site
December 18, 2014
WordPress 4.1 was launched by Dinah Washington. A new 2015 theme and multiple language option.
2014
Drupal developed by a community
January 1, 2015
Prestashop launched PrestaShop Cloud, a free self-hosted version of its software
February 24, 2015
Blogger announced that as of late March it will no longer allow its users to post sexually explicit content
February 28, 2015
Bloggers accounting for severe backlash from long-term bloggers
April 14, 2015
Shopify filed for an initial public offering (IPO) on the New York Stock Exchange and Toronto Stock Exchange
April 23, 2015
WordPress 4.2 was launched by Bud powell. Extended character support for mobile device.
August 18, 2015
Word press 4.3 launched by Billie Holiday. Optimization and Easy formatting.
October 7, 2015
Drupal 8 first release candidate (rc1) was announced.
November 3, 2015
Magento was spun out as an independent company by the new owner Permira private equity fund
November 19, 2015
Drupal 8.0.0 was released
2015
Sqaure space had reached $100 million in revenue and 550 employees.
2015
According to W3Techs, PrestaShop is used by 0.5% of all websites
March 21, 2016
joomla launches version 3.5-Contains download system information, category item counter, insert modules in articles, drag & drop images.
April 12, 2016
Word press 4.5lanuched byColeman Hawkins. Streamlined workflow, and live responsive previews.
August 16, 2016.
Word press 4.6 launched byPepper Adams. Streamline updates, native fonts, editor improvements ( Inline line checker, content recovery).
October 3, 2016
Shopify acquired Boltmade
November 1, 2016
Shopify partnered with Paystack
December 6, 2016
Word press 4.7 launched by Sarah vaughan. A new theme 2017, edit shortcuts, video headers, PDF thumbnails preview and dashboard in your language.
January 1, 2017
Shopify announced integration with Amazon
April 1, 2017
Shopify introduced a Bluetooth enabled debit and credit card reader for brick and mortar retail purchases
May 11, 2017
Shopify acquired Oberlo, which was one of the star applications on its own Shopify App Store
June 8, 2017
Word press 4.8 launched by Billy Evan. Exciting new widget ( image, video, audio and rich text), link boundaries.
September 19, 2017
Joomla launches 3.8- Contains Improved Routing System, Joomla 4 Compatibility Layer, Installable & Multilingual Sample Data, Code Improvements and Encryption Support
November 15, 2017
Word press 4.9 launched by Billy Tipton. Featuring design drafts, scheduling, and locking, along with preview links, the Customizer workflow improves collaboration for content creators
2017
Square space-Its 2017 ad won an Emmy Award for Outstanding Commercial.
May 1, 2018
Magento was announced that Magento would be acquired by Adobe for $1.68bn
September 1, 2018
Shopify announces plans to locate thousands of employees in Toronto’s King West neighborhood in 2022 as part of “The Well” complex
October 30, 2018
Joomla launches 3.9-Provides users with a comprehensive ‘Privacy Tool Suite’. This facilitates the compliance of Joomla websites with laws and regulations, most notably GDPR. The release includes over 250 improvements.
December 6, 2018
Word press 5.0 launched by Bebo.A new theme 2019, new block editor, classic editor,
2018
Squarespace partnered with the Madison Square Garden Company to launch the “Make It Awards”, which award $30,000 to entrepreneurs
January 2019
Shopify announced the launch of Shopify Studios
March 22, 2019
Shopify and email marketing platform Mailchimp ended an integration agreement over disputes involving customer privacy and data collection
April 2019
Shopify announced an integration with Snapchat
May 2019
Shopify acquired Handshake, a business-to-business e-commerce platform for wholesale goods.
June 2019
Shopify announced that it will launch its own Fulfillment Network
August 13th 2019
Joomla launshes version 3.9.11-Security release and minor bug fixes.
August 14, 2019
Shopify launched Shopify Chat
September 9, 2019
Shopify announced the acquisition of 6 River Systems
September 24th 2019
Joomla launches version 3.9.10-Security release and minor bug fixes.
October 2019
PrestaShop closed the Miami headquarters and ceased its operations in the Americas
1985
FileNet is considered as the First CMS introduced
1995
FileNet introduced a complete integrated document management suite of programs
August 23, 1999
Blogger was launched by Pyra labs
May 18, 2000
Drupal was introduced
2001
Drupal became an open source project
May 27, 2003
WordPress was Launched and b2/cafelog has about 2000 users. WordPress 0.7
February 2003
Blogger, Pyra labs was acquired by Google
2004
Shopify was Founded.
2004
Square space was introduced
2004
WordPress developed the capabilites by adding Plugins
January 3, 2004
WordPress 1.0 was lanuched by Miles Davis.Minimalistic interface with performance improvements.
May 22, 2004
WordPress 1.2 was lanuched by Charlus Mingus. Came with ability to manage and develop plugins.
October 2004
Blogger’s Pyra Labs’ co-founder, Evan Williams, left Google
2004
Blogger allows his users to post photos to their blogs
February 17, 2005
WordPress 1.5 was launched by Billy strayhorn. Themes and pages are introduced.
August 17, 2005
Joomla was Officially introduced
September 2005
Joomla released Mambo 4.5.2.3 that combined other bug and moderate-level security fixes.( version 1.0)
October 2005
WordPress Automatic manages to raise $1.1 million in funding.
December 21, 2005
WordPress 2.0 launched and a text editor was introduced.
2006
Wix was Offically launched.
June 2006
The Snowdevil founders launched the platform as Shopify
August 14, 2006
Blogger launched its latest version in beta
August 2006
WordPress first wordcamp annual is held in San fransico
December 2006
Blogger’s new version was taken out of beta.
Also Read
2007
Wix entered an open beta phase using a platform based on Adobe Flash.
January 22, 2007
WordPress 2.1 was launched by Ella Fitgerald. A new interface and an orthographic corrector.
May 2007
Blogger was completely moved over to Google operated servers.
May 16, 2007
WordPress 2.2 was launched by Stan Getz. Optimization of the loading speed of the CMS
September 24,2007
WordPress 2.3 was launched by Dexter Gordon. Tags and user notification for CMS updates.
July 2007- June 2008
Drupal.org site provided more than 1.4 million downloads of Drupal software, an increase of approximately 125% from the previous year.
January 22, 2008
Joomla launched version 1.5
March 29, 2008
WordPress 2.5 was launched by Micheal Brecker. Improved UI and Widgets
July 15, 2008
WordPress 2.6 was launched by McCoy Tyner. Post revisons, word counts, image captions, theme previews and reordering of galleries.
December 10, 2010
WordPress 2.7 was launched by John Coltrane. Streamlined performance.
2008
WordPress won, Winner of InfoWorld’s “Best of open source software awards: collabration”.
2008
Magento won the “Best of open source software adwards” and ” SourceForge community choice Awards”
March 5, 2009
Drupal-Buytaert announced a code freeze for Drupal 7 for september 1, 2009
June 11, 2009
WordPress 2.8 was launched by Chet Baker. Browse Entire theme directory, single click theme install and code press editor.
December 18, 2009
WordPress 2.9 was launched by Carmen McRae. Global undo/trash feature, built-in image editor, batch plugin update.
From 2009-2012
Sqaure space grew an average of 266% in yearly revenue.
February 2010
WordPress unveils wapuu, their official mascot at wordcamp Fukuoka.
April 2010
Shopify launched a free mobile app and Apple app store.
2010
WordPress is the Winner of digitalsynergy’s “Hall of fame CMS category in the 2010 open source”
May 2010-April 2012
Prestashop grew from 17 employees to more than a hundred.
January 5, 2011
Drupal 7 was released with release parties in serveral countries.
January 10, 2011
Joomla adds a full access control list functionality plus, user-defined category hierarchy, and admin interface improvements. ( version 1.6)
February 23, 2011
WordPress 3.1 launched by Django Reinhardt. A new admin bar and improved taxonomy.
March 2011
Wix had 8.5 Million users and raised $40 Million.
June 2011
Wix launched the facebook store module, making its first step into the social commerce trend.
July 4, 2011
WordPress 3.2 was launched by George Gershwin. Fastera nd lighter with improvement typography, design and code.
July 19, 2011
Joomla adds enhanced security and improved migration tools. ( version 1.7)
December 12, 2011
WordPress 3.3 was launched by Sonny stitt. New drag-and-drop uploader, hover menus and pointer tips.
January 24, 2012
Joomla launches version 2.5-This version was the first to run on other databases besides MySQL (version 2.5)
November 6, 2013
Joomla launches version 3.2- Highlighting Content Versioning (version 3.2)
2013
The drupal website listed hundreds of vendors that offered Drupal-related services.
2014
Another funding round confirms that automatic is worth $1.16 billion.
April 1, 2014
it received another $40 million in funding
April 30, 2014
Joomla launches 3.3- Improved password hashing and microdata and documentation powered by MediaWiki Translate extension. (version 3.3
May 15, 2014
Wix launched the WixHive API which allows Wix apps within a user web site
December 18, 2014
WordPress 4.1 was launched by Dinah Washington. A new 2015 theme and multiple language option.
2014
Drupal developed by a community
January 1, 2015
Prestashop launched PrestaShop Cloud, a free self-hosted version of its software
February 24, 2015
Blogger announced that as of late March it will no longer allow its users to post sexually explicit content
February 28, 2015
Bloggers accounting for severe backlash from long-term bloggers
April 14, 2015
Shopify filed for an initial public offering (IPO) on the New York Stock Exchange and Toronto Stock Exchange
April 23, 2015
WordPress 4.2 was launched by Bud powell. Extended character support for mobile device.
August 18, 2015
Word press 4.3 launched by Billie Holiday. Optimization and Easy formatting.
October 7, 2015
Drupal 8 first release candidate (rc1) was announced.
November 3, 2015
Magento was spun out as an independent company by the new owner Permira private equity fund
November 19, 2015
Drupal 8.0.0 was released
2015
Sqaure space had reached $100 million in revenue and 550 employees.
2015
According to W3Techs, PrestaShop is used by 0.5% of all websites
March 21, 2016
joomla launches version 3.5-Contains download system information, category item counter, insert modules in articles, drag & drop images.
April 12, 2016
Word press 4.5lanuched byColeman Hawkins. Streamlined workflow, and live responsive previews.
August 16, 2016.
Word press 4.6 launched byPepper Adams. Streamline updates, native fonts, editor improvements ( Inline line checker, content recovery).
October 3, 2016
Shopify acquired Boltmade
November 1, 2016
Shopify partnered with Paystack
December 6, 2016
Word press 4.7 launched by Sarah vaughan. A new theme 2017, edit shortcuts, video headers, PDF thumbnails preview and dashboard in your language.
January 1, 2017
Shopify announced integration with Amazon
April 1, 2017
Shopify introduced a Bluetooth enabled debit and credit card reader for brick and mortar retail purchases
May 11, 2017
Shopify acquired Oberlo, which was one of the star applications on its own Shopify App Store
June 8, 2017
Word press 4.8 launched by Billy Evan. Exciting new widget ( image, video, audio and rich text), link boundaries.
September 19, 2017
Joomla launches 3.8- Contains Improved Routing System, Joomla 4 Compatibility Layer, Installable & Multilingual Sample Data, Code Improvements and Encryption Support
November 15, 2017
Word press 4.9 launched by Billy Tipton. Featuring design drafts, scheduling, and locking, along with preview links, the Customizer workflow improves collaboration for content creators
2017
Square space-Its 2017 ad won an Emmy Award for Outstanding Commercial.
May 1, 2018
Magento was announced that Magento would be acquired by Adobe for $1.68bn
September 1, 2018
Shopify announces plans to locate thousands of employees in Toronto’s King West neighborhood in 2022 as part of “The Well” complex
October 30, 2018
Joomla launches 3.9-Provides users with a comprehensive ‘Privacy Tool Suite’. This facilitates the compliance of Joomla websites with laws and regulations, most notably GDPR. The release includes over 250 improvements.
December 6, 2018
Word press 5.0 launched by Bebo.A new theme 2019, new block editor, classic editor,
2018
Squarespace partnered with the Madison Square Garden Company to launch the “Make It Awards”, which award $30,000 to entrepreneurs
January 2019
Shopify announced the launch of Shopify Studios
March 22, 2019
Shopify and email marketing platform Mailchimp ended an integration agreement over disputes involving customer privacy and data collection
April 2019
Shopify announced an integration with Snapchat
May 2019
Shopify acquired Handshake, a business-to-business e-commerce platform for wholesale goods.
June 2019
Shopify announced that it will launch its own Fulfillment Network
August 13th 2019
Joomla launshes version 3.9.11-Security release and minor bug fixes.
August 14, 2019
Shopify launched Shopify Chat
September 9, 2019
Shopify announced the acquisition of 6 River Systems
September 24th 2019
Joomla launches version 3.9.10-Security release and minor bug fixes.
October 2019
PrestaShop closed the Miami headquarters and ceased its operations in the Americas
2019
PrestaShop received the Acteurs du Libre International Award for its international development strategy.
January 28th 2020
Joomla launches version 3.9.11-Security release and minor bug fixes.
February 21, 2020
Shopify announced it would join the Libra Association
Basically, CMS has changed the way we interact with digital content. It’s been around since the late 90s or early 2000s, when static HTML pages were the norm, but it wasn’t until the late 2000s and early 2010s that CMS platforms started popping up that content management really took off. It’s made content management more accessible and easier for people to use, and it’s had a huge impact on how we interact with it. We as a WordPress development services company, know how much it’s changed the way we do web development and manage content.
Looking for WordPress Development Services?
Seize and experience the transformative impact of WordPress solutions with ColorWhistle.
In quest of the Perfect WordPress Solutions Buddy?
Be unrestricted to click the other trendy writes under this title that suits your needs the best!
- WordPress Website Digital Marketing Tips
- How to Create a Medical Website in WordPress?
- Top WordPress Website Design Ideas and Inspirations
- Start with Wix, Switch to WordPress – How to Decide?
- WordPress Facts And Myths (We Bet You’ll Be Amazed!)
- WordPress Responsive Theme Development With Bootstrap
- How to add audio file to the WordPress website





